Mobile App Security: What is it? How to secure mobile apps

With mobile app risks on the rise, businesses must prioritize mobile app security to prevent threat actors from spying on their confidential or sensitive data.
Mobile devices have surpassed workstations and laptops in popularity. In addition to being portable, technological advancements have enabled them to perform virtually identical functions to desktops. According to Techjury.net, mobile users have increased by over 10% in the past year, and users in the U.S. spend nearly 51% of their time online on mobile devices.
Users engage in nearly all activities on their mobile devices. Through these applications, businesses can collect useful information about users, such as their location, usage statistics, phone number, likes, dislikes, and other meaningful metrics. If the information on these mobile devices falls into the incorrect hands, it could be detrimental to the user. Consequently, the need for mobile app security is now unavoidable.
I. What is Mobile Application Security?
Mobile app security is the practice of protecting high-value mobile apps and your digital identity from all types of fraudulent attacks. This includes tampering, reserver engineering, malware, key recorders, and other forms of interference or manipulation. A comprehensive mobile app security strategy comprises technological solutions, such as mobile app shielding, as well as usage guidelines and business processes.
Mobile app security has grown in importance in the modern era. A breach in mobile app security can not only grant hackers access to a user’s private life in real-time, but also expose sensitive information such as their current location, banking information, and more.
II. Mobile Apps Hacking Statistics
Consumers frequently rely on organizations to evaluate their mobile app security measures before making them accessible. However, IBM’s research uncovered startling realities.
- 50% of enterprises have no budget for securing their mobile applications.
- 40% of businesses do not examine the code of their mobile applications for security flaws.
- In 2014, cyberattacks compromised 1 billion personal data records, and at any given time, mobile malware affects 11.6 million mobile devices.
- On average, less than half of the mobile apps developed by a company are tested, and 33% are never tested for mobile app security.
The aforementioned figures provide sufficient motivation for hackers to exploit flaws in mobile app security, and they attempt to exploit any or all unsecured codes.
III. Why Must We Secure Our Mobile Apps
Weak mobile app security can have various short- and long-term consequences for your business.
1. Loss of customer information
If hackers obtain access to sensitive customer information, such as login credentials or account information, your business could suffer severe consequences, including customer churn and financial loss.
2. Revenue loss
When one-time password (OTP) authentication is not required, hackers can obtain credit or debit card numbers and manipulate bank transactions. Such attacks can destroy your business if you’re a finance or financial company.
The vulnerabilities can also be exploited to gain access to premium features without paying for them. Consequently, you must ensure mobile app security at every stage and safeguard your organization’s data.
3. Brand confidence
Due to poor mobile app security, you risk losing consumer trust. When customers abandon a business as a result of a security incident, the loss is irreparable because it is extremely unlikely that they will return. This, in turn, harms their brand image and brand confidence.
4. Compliance and regulatory issues
Most app compliance certificates and regulatory documents include mobile app security requirements and best practices. If your mobile app security falls short of these compliances, or if you lose data or fall victim to an attack due to app vulnerabilities, your business will be wiped out by massive lawsuits.
Also read: Mobile app hosting costs: Everything You Need to Know 2023
IV. Most Common Risks in Mobile Apps Security
It is far too simple to compromise mobile app security. Companies desire rapid app releases, but development teams are frequently understaffed and overcommitted. Security is neglected, although it should not be. You must pay close attention to the following 9 mobile app security risks if you wish to safeguard your company’s reputation and revenue.
1. Low API Protection
If you are developing an application, you will almost undoubtedly use at least one API. A mobile app API enables one application to retrieve data from another. For instance, it is what enables a travel booking website to compile information from various hotels and airlines in an organized manner. It is also what enables Google Maps to display directions to a given location.
Most modern applications rely heavily on APIs for their functionality. Numerous developers fail to secure their APIs. They believe that bad actors will not find them engaging, but the converse is true. APIs provide access to stable, structured data, which is precisely what malicious actors desire. They will reverse-engineer your API to determine which endpoints your application utilizes, execute your application with an emulator, or utilize a mobile farm to locate access points.
How to prevent low API protection
As with many of the other hazards on this list, malicious bots pose the greatest risk of exploitation. Generally speaking, bots have no reason to use your API, so its usage is not a positive sign. A bot protection solution designed particularly for mobile app security will be able to detect and block malicious bots while allowing legitimate ones to pass.
2. Insufficient server-side controls
Modern mobile apps consist of both a client and server side. The client-side is visible to the user. This is the user interface, complete with animation and functionality. The client side relies on the server side, which is responsible for ensuring that everything functions correctly, for everything to work. Client and server typically interact via an API.
Common server-side vulnerabilities are readily exploitable via the frequently insecure API. They can include faults in code logic, weak authentication rules, insecure server configurations, and access control vulnerabilities, among others. They generally fall into 2 categories: code vulnerabilities and configuration vulnerabilities.
How to prevent insufficient server-side controls
Although the client side of an app communicates with its server side via an API, you can block numerous threats by preventing automated routines from accessing your API. While this won’t prevent manual attacks or fix server-side vulnerabilities, it will at least prevent your mobile app security from being exploited very readily.
3. Injected on the client side
Unusual data that leads to unauthorized access is one method an adversary can use to attempt to compromise your application. This data is typically transformed so that your application can interpret it as executable code. An assailant could, for instance, target a mobile SQL database by inserting a creative query that retrieves private data from other users.
SQL intrusions are only one client-side injection type. Local File Inclusion is another form, in which an attacker uploads an executable file that your app reads and executes, which can cause your app to malfunction or expose sensitive data.
How to prevent client-side injections
One of the most effective ways to prevent client-side injections is by performing appropriate input validations, i.e., checking all incoming data (including that from partners, regulators, and suppliers) to ensure that it falls within the expected parameters. Effective input validation can entail:
_ Putting into effect a minimum and maximum value range verification for data and string length.
_ Introducing a regex check that avoids “any character” wildcards such as “.” and “*”.
_ Requesting an exact match if the input data options are static.
_ Accepting only input data from a list of permitted values.
4. Insecure Storage of Sensitive Data
Frequently, mobile apps, including financial apps, store sensitive data locally. This means that your PIN, credit card numbers, passwords, login information, and other sensitive data are merely stored on your smartphone. Worse yet, they are frequently stored insecurely. If a tech-savvy individual obtains access to your device (remotely or otherwise), they can locate and steal all of your data.
Often, sensitive local data is stored insecurely due to inadequate encryption. Some mobile apps do not encrypt local data at all, which is the gravest violation. Other mobile applications encrypt local data but do not properly store the encryption keys, or they employ insecure custom encryption protocols.
How to prevent unsafe sensitive data storage
Data at rest must be adequately encrypted using a robust encryption protocol that has been widely regarded as secure by the mobile app security community for a long time. Do not attempt to perform complex actions with a custom protocol. It is much more likely that you will make a mistake and inadvertently expose sensitive local data instead of safeguarding it.
5. Hardcoded keys or a password
This is the most elementary error, but it still occurs. To make an app simpler to implement, maintain, and investigate, developers frequently hardcore passwords, API keys, or OAuth keys. This indicates that these credentials or keys are encoded explicitly within the code. When these hardcoded values are discovered because an attacker reserve-engineered your app, you leave yourself broadly open to exploitation of all kinds.
How to prevent hardcoded keys or a password
Provide developers with a password management solution that securely stores their passwords and credentials so they do not need to hardcode sensitive values. In addition, scan frequently for hardcoded passwords, and if you discover one in a live application before anyone else, promptly patch the issue so that no one can exploit it.
6. Insecure source code
The app’s source code is what makes it functional. It’s the fundamentals. If you do not protect your source code, you are effectively giving away your competitive advantage, or intellectual protocol, for nothing. In addition, source code frequently coexists with API or encryption keys, authentication credentials, user passwords, and other sensitive information that must not be exploited.
We do not only mean your source code when we refer to source code. We refer to all of the source code you employ, including code from third parties such as partners or suppliers, as well as straightforward open-source code. If any of these components are insecure, your mobile app security is at risk.
How to prevent insecure source code
You can prevent insecure source code by utilizing mobile app security testing tools that examine your source code frequently or even continuously for vulnerabilities. This can perform most code review work, but you should still conduct manual code evaluations to identify vulnerabilities. Additionally, you should retain your source code securely and grant access to it only to those who require it.
7. Leakage of sensitive data
Data leakage is the exposure of sensitive data online, whether by accident or design. This is what happened to the popular mobile parking app Parkmobile when a third-party software vulnerability led to a data breach that exposed the emails, dates of birth, license plate numbers, and phone numbers of more than 21 million users.
Occasionally, these breaches occur unintentionally. Firebase, for instance, is one of the most popular data storage solutions for Android apps, but it is frequently inadequately configured. Anyone with the correct URL can readily access the databases of an app built with Firebase, exposing sensitive user data.
How to prevent leakage of sensitive data
One method to prevent the leakage of sensitive data is to prevent data caching. Cache-stored data can be used by adversaries to attempt to gain access to a user’s account. Users can explicitly clear the cache, or developers can choose not to cache sensitive data. It may be slightly more inconvenient for the consumers, but it certainly results in a more mobile app security.
8. Data transmission that is unsafe
Unencrypted or inadequately encrypted data at rest is insecure, so it should come as no surprise that unencrypted data in transit is also insecure. It is not difficult for an adversary to intercept data as it travels over wifi (especially insecure public wifi) or the carrier network of a mobile device.
Although data in transit is frequently encrypted, it is frequently poorly configured, the keys are improperly managed, or the developers use an outdated encryption algorithm. In essence, the same issues as with unencrypted or inadequately encrypted data at rest, with the exception that hackers gain access to it via various channels.
How to prevent unsafe data transmission
Use SSL or TLS protocols to transmit data. Even better, encrypt data before sending it through SSL or TLS, so that there is a second layer of mobile app security in case the SSL or TLS protocol is vulnerable. Moreover, protect data in transit from man-in-the-middle (MitM) assaults with the correct certificate validation and authentication.
9. Insufficient tracking and logging
Once your program is live, you want to track its performance. You need to recognize when mobile app security issues arise so you can respond without negatively impacting the user experience. But you won’t be able to do any of that if you don’t have adequate logging and monitoring systems in place. You will instead be left in the shadows, with information gaps that prevent you from defending against mobile app security incidents.
How to prevent insufficient tracking and logging
The mobile app security solution is to implement or develop a system that logs and monitors all critical application variables. This includes launch time, UI response time, crashes, battery consumption, data consumption, and other mobile app security concerns.
You can also read App Development Timeline: How Long Does It Take To Make an App?
V. Best Practices of Mobile App Security
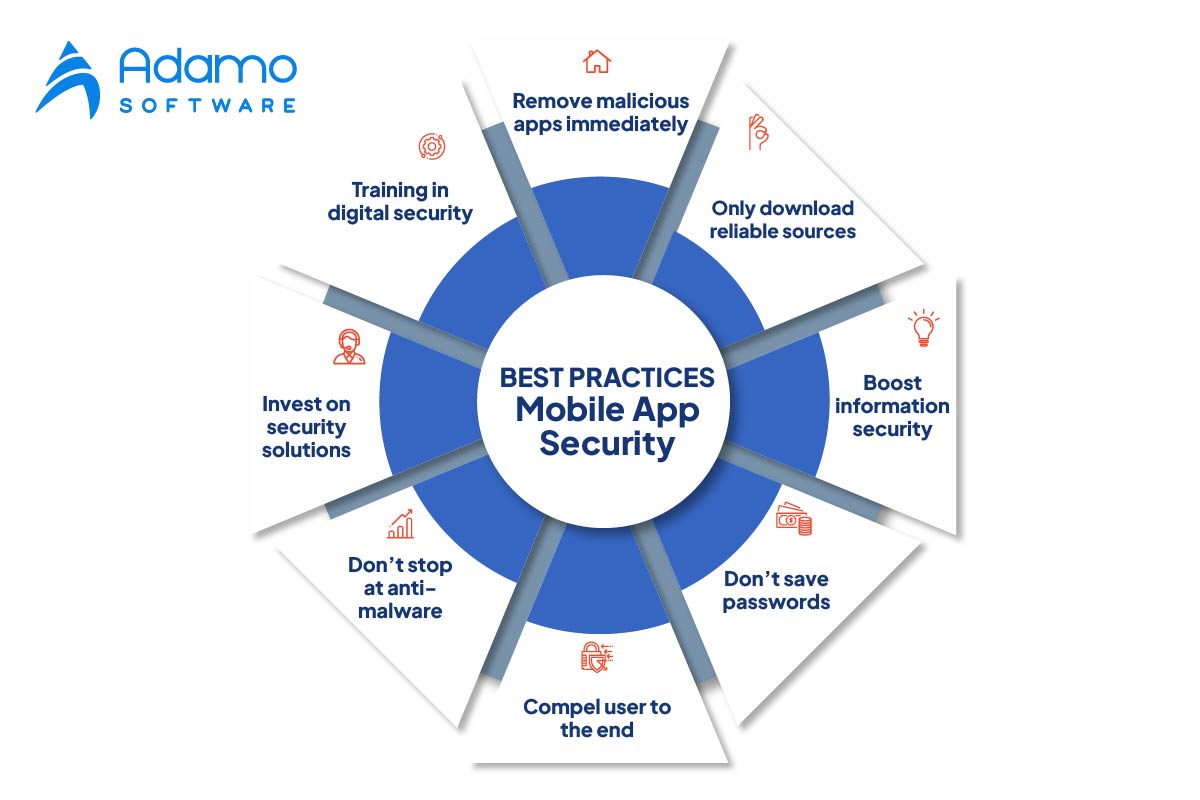
1. Implement training in digital security
Educate your employees on the dangers posed by mobile app security. Teach them how to identify potential mobile app attacks, malicious websites, and phishing attempts, and implement the appropriate response procedures.
2. Keep an eye out for inappropriate applications
Keep a close watch on both authorized and unauthorized app download platforms for apps containing your brand’s name, logo, or messaging that may have been posted to entice unwitting customers. Remove malicious apps immediately.
3. Download only from reliable sources
Provide your employees and customers with a list of verified app download sites. Even then, tell them to be very careful when downloading new apps and to report any suspicious mobile app security behavior.
4. Boost Information Security
Establish a brand-specific mobile app security strategy and a policy mandating the active collection and resolution of all potential data breaches. Have your development or IT team implement strong encryption when transferring data between devices.
5. Don’t Save Your Passwords
Does an app require a username and password for login? Discourage the use of apps that store passwords on your system or in the cloud, as this can enable private credentials to be harvested and used to compromise other devices or networks.
6. Compel the user session to the end
Never allow a user’s session to remain active after logging out or closing your application. Require them to end the session every time they log out and to re-login to regain access. Additionally, after a predetermined period of inactivity, log the user out for added mobile app security.
7. Don’t Stop at Anti-Malware
Numerous mobile app security resources predominantly scan devices for known malware and alert the user with the option to remove anything that is discovered. Although this is an excellent precaution, your company’s digital security should not end here. Include encryption procedures, instruments for behavioral analysis, traffic monitoring, and more.
8. Spend money on mobile app security solutions.
Your team can only do so much to ensure the mobile app security. You can augment your defensive capabilities by employing a mobile app security suite that manages most app monitoring, data analysis, and rouge app takedown.
VI. Adamo – Bring Secure Mobile App Solutions
As a leading software development company in Vietnam, Adamo Software has a chance to work with different startups and entrepreneurs in many industries. We all know that such innovative applications like mobile apps need to be secured to protect end-users’ data and business operations. Explore our mobile app development services for your business ideas.
With this article, we provide necessary information related to mobile app security and hopefully, it will help you to develop mobile apps in the future. If you have any questions about building a mobile app, do not hesitate to contact us.