Cybersecurity ecosystem: Breaking the current standard

Since the world operates as a huge machine, cybersecurity ecosystem or security ecosystem are extremely invested in protecting users’ benefit against cyberattacks.
The consideration of cybersecurity and cyber threats are taken into account when severe malware attacks targeted company systems these days. 2020 cybersecurity reported that over 18,000 businesses and even government departments faced infiltration by hackers in the US alone.
Additionally, along with malware attack become more sophisticated, data processing to the internet every second are facing risky, which harm user privacy. In this situation, the demand for a cybersecurity ecosystem is unmistakable, that both public and private sectors need software development solutions for assuring national and international security.
What is cyber security
For embracing several players, cyber security indicated different positions and meaning to players, including private companies, regulation sectors, users, processes, cybersecurity providers, and more. Accordingly, depending on each purpose, the cyber ecosystem introduces separated attributes.
Cyber ecosystem definition
The cyber ecosystem is believed to adjust the relationship among participants within the cybersecurity infrastructure. In fact, you cannot ignore the interaction of linked entities in a cyber ecosystem that is remarkably similar to animals in the natural ecosystem. Accordingly, those individualities showed within the communication induce a vulnerable environment to unauthorized acts. Expressly, without a proper security level in the ecosystem, hackers could handily steal data, personal identities, and business secrets.
Additionally, the core purpose of a healthy cyber ecosystem refers to keep participants working smoothly, while it deters the threat actors intruding the system.
Cybersecurity in digital ecosystem
In the digital ecosystem, companies target keeping the process of information exchange secured, which is called continuous monitoring. By controlling the various solution linking within the system, it is required software development,which automatically scans and detect potential security vulnerabilities to protect the assets of users and business (i.euser identities, secret information, payment details, etc.)
As mention above, the future of the cybersecurity ecosystem relying on automation. Evidently, considering authentication and interoperability, the cyber ecosystem health could be guaranteed by speeding up protection acts and optimizing their intervention efficiency simultaneously. Basically, cybersecurity in the digital ecosystem includes series of layered defenses, which are methods and algorithms to identify the attackers. Automation could help the cybersecurity system to steadily learn and adapt without the direct execution of dedicated developers
The role of cybersecurity ecosystem in the IT industry
In recent years, several significant attacks target corporations and government arms alarmed the role of cybersecurity in the entire IT system. In the US, AMCA faced a payment portal hack, which leaked roundly 24 million accounts. Reports claimed that at least 20 healthcare institution has adverse affected due to the accidents. Besides in the UK, the British Airway confirmed a breach in its website. Evidently, the credit card information of customers had been stolen, which damaged the brand image.
Accordingly, to cyber-attack incidents, payment and financial software solutions were reported as the most vulnerable targets. Followingly, education software and cloud services were the second runners, commonly coped with external attacks.
Understanding the crucial role of the cybersecurity ecosystem in the IT industry suggests the idea of a future resilient environment for real-time prediction and heal cyber loopholes. Hence, stalwart cybersecurity is expected to defense devices by deterring the spread of attacks. Besides, the system combining software development solutions is needed to assure secured exchange of information.
Component of the security ecosystem
Obviously, the cybersecurity ecosystem consists of complex components, which need to integrate into an independent system to form a comprehensive solution. The component selection would be depending on business priorities and strategies. Basically, IDS, SIEM, and PAM are believed as three key touchpoints for a well-operated security ecosystem.
1. Intrusion detection system (IDS)
IDS focuses on detecting any potentially harmful activities that occurred in the network traffics. Accordingly, IDS is responsible for control all traffic and keep them away from policy violations. In the current standard, a typical IDS would perform in two fundamental methods:
_ Anomaly-based IDS helps owners detect and deter malware attacks by leveraging Machine learning. Accordingly, software developers or ML engineers would build an activity model that arises on the system would be compared with the sample model. Any suspicious incidents would be investigated to keep the system safe.
_ Signature-based IDS includes a library of a specific pattern or detected malicious instruction sequence. Those are called signature that any activities show its similarities with available signature will be capture as a malware attack. In fact, signature-based IDS consists of a significant drawback that this system has struggled in detect novel malware.
2. Security information and event management (SIEM)
The SIEM system is currently used to track and analyze the whole activity inside an IT infrastructure. SIEM is known as the combined concept of security information management (SIM) and security event management (SEM). While SIM performs data-related tasks, including data collection and data reporting, SEM manages the system on a real-time basis to instant detect threats.
Due to performing tasks with data, Artificial Intelligent (AI) and Machine learning (ML) is contributed as key in many SIEM products. Accordingly, the SIEM system enables secured data collection from multi-sources.
3. Privileged Access Management (PAM)
PAM system specialties software and technologies in controlling user permission to access parts of the IT environment, including account, system, and process. With the PAM system, owners have the right to decentralize access into several levels that are believed to prevent external attacks.
PAM consists of clearly defined access rights for authorized any activity arising on the system. Basically, in a standard PAM system, user accounts could be separated into 2 levels:
_ Guest accounts have lower access permission with some restrictions in accessing resources.
_ Standard user accounts have a moderate access right to enter some certain types of assets. Standard accounts have more power than guest accounts in term of privileges
Cybersecurity ecosystem challenges
Across this decade, the IT industry has indicated a dramatically sophisticated innovation with blockchain, 5G network, augmented reality, and Artificial Intelligence. Along with those points of pride, it induces a threat for the cybersecurity ecosystem with a high level of vulnerabilities with hacks and attacks. Moreover, in the new decade, the cybersecurity ecosystem is claimed to be harm by series of challenges, which urgently needs improvement to limit future cybercriminals.
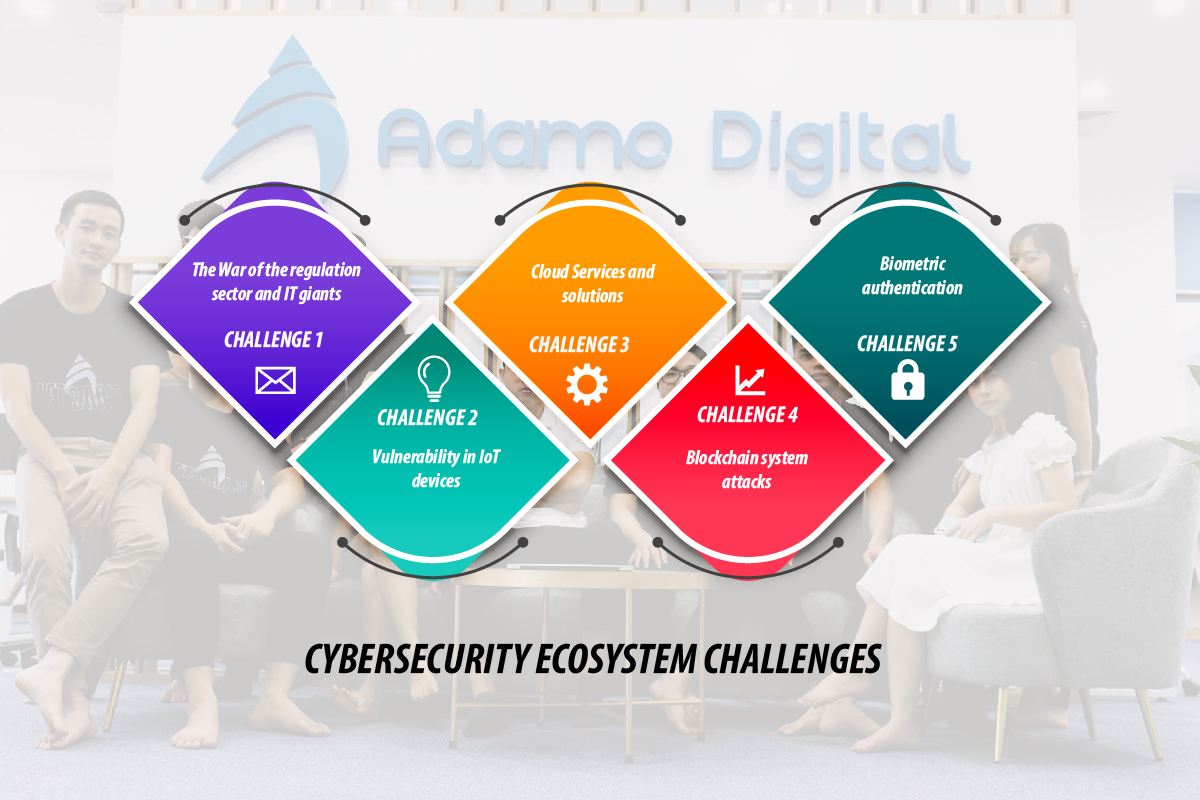
1. The War of the regulation sector and IT giants: in 2018, the EU imposed General Data Protection Regulation (GDPR) on companies operating with RU citizens, which was seemingly a strict regulation extreme affected several systems. Many companies need a novel upgrade to meet requirements. Companies that violated the compliance would be fined roundly US$ 25 million. In 2021, the Australian government and Facebook are not coming with an agreement for profit sharing. Also, IT giants in America have to take on privacy hearings. Undeniable, regulation sectors got struggling with the IT industry growth, that the change in policies would influence unexpected results to the innovated cybersecurity ecosystem.
2. Vulnerability in IoT devices: the number of cyberattacks targeting at smart-devices is predicted to increase in 2021, due to under mature period of IoT device development. Undoubtedly, those IoT devices in the market have suffered a low level of fulfillment, especially for home and office devices. Since companies are in the initial stage of device development, it remains series of undetectable errors exploited by cybercriminals. Hence, improve security levels within IoT devices would be a pressing challenge for dedicated software developers.
3. Cloud Services: Undoubtedly, the current world has belonged to the cloud solution, where a large part of data is transferring by cloud services hourly. Unfortunately, cloud services are also the preferred target of cyber-attacks due to the large amount of valuable data stored in them. Expressly, integrated API not under trusted organization control refers to be vulnerable to hackers and remains series of security issues.
4. Blockchain system attacks: currently, reports pointed out three popular types of attacks faced by blockchain systems, which are Eclipse attack, Sybil attack, and DDoS attack. Eclipse attack attempt to take control of the connection. Sybil Attack to steal identities. On the other hand, DDoS attacks remarkably focus on cryptocurrency owners. Indeed, the fundamental of those attacks basically causes financial losses to businesses.
5. Biometric authentication: one of the significant issues of using biometric algorism for security is that they can handily duplicate or stolen by cybercriminals. In this case, the real owners will get struggling to protect their assets since their biometric cannot be changed.
The new standard in the innovation cybersecurity ecosystem
The global tech shock after COVID 19 might cause the regulation sector to scarify the concern regarding cybersecurity in favor of public health consideration. Accordingly, governments have a high incentive to using technology innovation in detecting and identifying infected people without the significant concern about personal identities breaches. In fact, many experts emphasize how much the pandemic supports the rise of cybersecurity globally.
To illustrate this point, last year, when social distancing policies force the large share of global workforces working with online meetings and online conferences, the number of Zooms (a video conferencing app) accounts had seen a dramatic increase. Unfortunately, roundly 0.5 billion accounts were believed to be stolen by cybercriminals to the public on the dark web. The changing in government preferences would lead to significant disruption in the cybersecurity ecosystem from 2021.
On the other hand, according to CSC, several country leaders are considering building a typical behavior in cyberspace. When novel regulations would be imposed in adjusting party behaviors, mentioned movements expectedly reshape the cybersecurity ecosystem. As a result, the shape behavior would affect military power used in the internet security, private sector operation, and reforming government.
Final Thoughts
Undeniably, an innovation cybersecurity ecosystem is indispensable for protecting the national cyber-health. Several debates regarding how the public and private sectors react to the future threat of cybersecurity remain. As the leading software development company in Vietnam, Adamo Software helps firms surpass infrastructure development. It is time to thoroughly move into the profound evolution of the cybersecurity ecosystem across the world.