How to secure api: The 10 most dangerous API risks to avoid

API security has become increasingly important, especially now that so much work in computer systems involves using APIs to send messages between systems. API stands for application programming interface. It is a software application that can pass information and perform actions with another software application. However, APIs could be exploited and suffer data violations and intrusions. It is critical to protect both APIs’ reach and deliveries to improve application protection and ensure data remains trustworthy.
This article will reveal the definition of API security and describe REST and SOAP API security differences. We also consider the 10 most dangerous API risks and explain how to secure API successfully in 7 steps. If you opt for APIs or handle APIs, understanding how to ensure API is important. It helps to secure your edifice.
I. What is API security?
API security is all about measures that can be put in place to secure APIs against hackers, malicious attacks, and data leaks. APIs are interfaces enabling different applications to share data. For that reason, they are points of cyberthreat entry. An attacker can gain access to resources, modify them, or induce resource depletion if APIs are not shielded. As it was seen, understanding how to secure API endpoints against such points of attack is paramount in eliminating them.
API security deals with the protection of the link between distinct applications. This includes identifying who is allowed to use the API (Authentication), whether they are allowed to do so (Authorization), and whether the data transfer is secure (Encryption). By doing the following, organizations can go a long way to minimizing the chances of a breach.
To comprehend these aspects in detail, several threats that may occur when working with APIs should be mentioned. These threats include unauthorized data access, weak authentication, injection, or denial of service. These risks are solved by security methods such as API gateways and rate limiting. API security is well understood as an element of cybersecurity. And its goal is to make APIs effective and safe.
Finally, API security secures APIs against threats to prevent unauthorized access to data and systems. Understanding how to protect APIs will eliminate vulnerabilities and protect users and organizations from cybercriminals.
Also read: What is mobile API testing? A comprehensive overview of API testing app
II. REST vs. SOAP API security
It is imperative to begin by distinguishing REST from SOAP, the two most popular API protocols. REST and SOAP have different working models due to their organic structures and the approach to data delivery.
1. REST API Security
REST is an easy and adaptable style that integrates well with HTTP. Hence it is fond of web services. Though REST does not inherently have security provisions, developers must layer these for security. HTTPS is often used to secure data transfer, while OAuth is used for authentication and API keys for authorization. One of the drawbacks of REST is that, while it is simple, APIs are more exposed if best practices are not employed. Specifically, validating inputs or limiting the data shared through the REST API is crucial. Proper management of authentication tokens is also vital. In the REST environment, the issue of secure APIs is a continuous learning process that needs additional tools.
2. SOAP API Security
SOAP is more elaborate and rigid than the others and has integrated security measures from WS security principles. SOAP does support encryption and digital signatures to ensure the integrity and confidentiality of the message. Therefore, it is appropriate for scenarios needing more stringent security than others, like financial transactions. SOAP is used more often than REST. It has more layers of security built-in by default. Also, it uses a structured messaging format such as XML, which is more secure or “out-of-box.” However, this makes it less flexible and can complicate its implementation and site management.
In choosing how to secure APIs, REST is more suited than SOAP based on the letter’s security need. Manual security measures must be implemented with REST but are easier to scale and implement in different systems and applications. For one, SOAP possesses built-in security more robust than TSwS, but it incurs higher complexity and overhead charges.
III. Explore Top 10 API security threats
A look at the practical aspect of securing APIs is useful to common security threats targeting APIs. Awareness of such risk factors means developers and other organizations can guard against such threats to the systems they create. Here are the top 10 API security threats to be aware of:
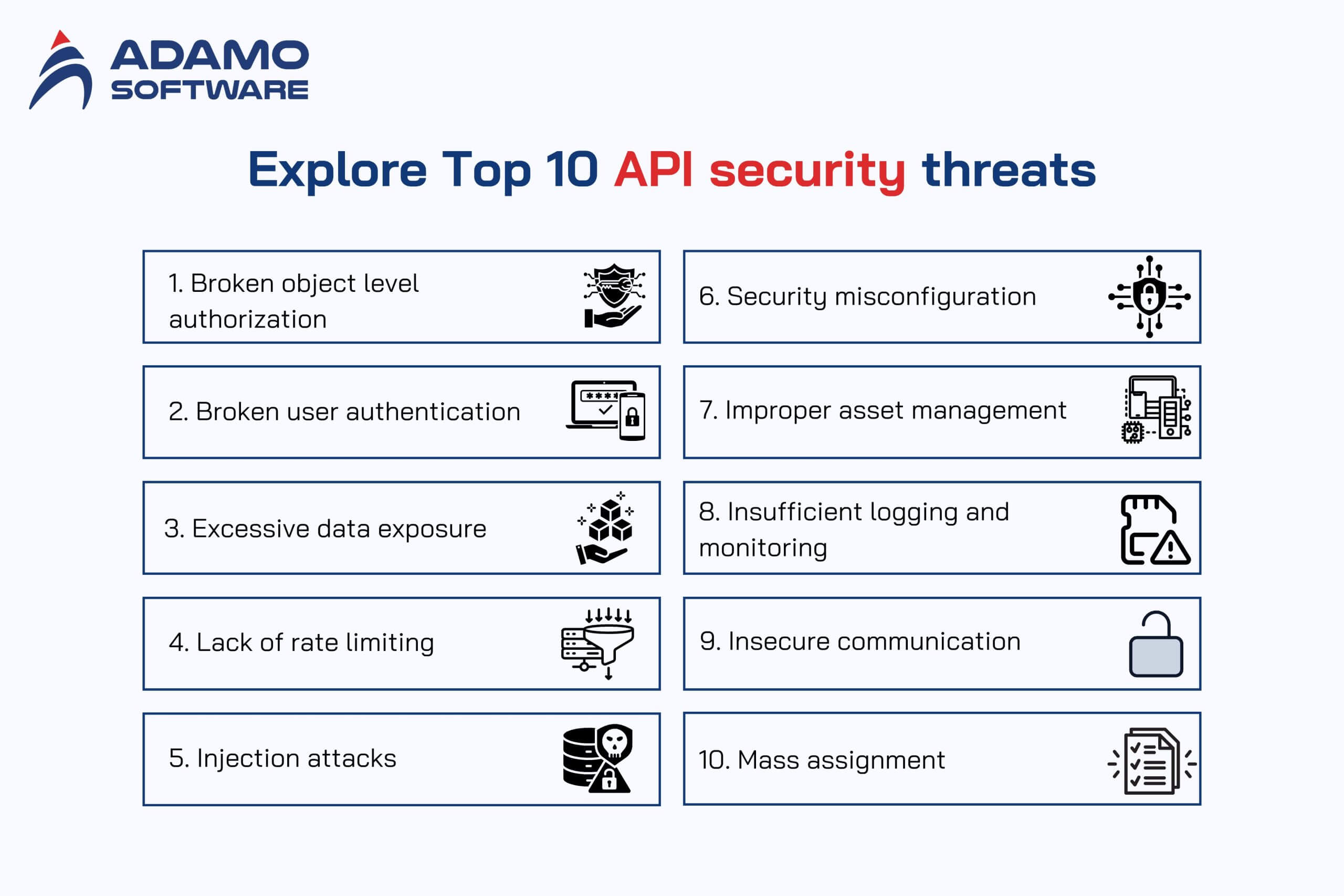
1. Broken Object Level Authorization
When APIs fail to adequately limit access to the object in question, this happens. Attackers can make up object IDs to achieve access to secure information. To protect API against this, there needs to be strict authorization checks and validation that form part of both API design and API gateway.
2. Broken User Authentication
Lack or inadequate compliance with the authentication process exposes the system to the vulnerability of unauthorized access. API authentication might have weak points, which attackers will use to mimic licit users. To address this, ensure strict authentication like multi-factor authentication (MFA).
3. Excessive Data Exposure
On some occasions, APIs release large amounts of information, often including information that could prove sensitive to others, without the possibility of eliminating all irrelevant details. The response should only include the required data for a particular request, and responses should be sanitized to enhance how to secure APIs efficiently.
4. Lack of Rate Limiting
In more recent events, there was even a case where API was flooded with more requests, and it was transformed into a Denial of Service (DoS) attack. It is seen that application rate limits and throttling provide better performance and security.
5. Injection Attacks
APIs are also prone to injection attacks such as SQL injection where the data given is wrong in a manner that makes the API perform operations that are undesirable. For instance, get input validation and proper sanitation rights to learn how to secure API against such threats.
6. Security Misconfiguration
Configuration errors, like turning the security option off or failing to update the API software, make different APIs vulnerable. This way the security is checked and updated for the settings to be properly set up.
7. Improper Asset Management
APIs untracked or simply forgotten can be the source of security gaps. Maintaining a full list of APIs and regularly reviewing them are important concerns in how to secure API systems.
8. Insufficient Logging and Monitoring
When logging is not properly done, it becomes complicated to identify security intrusions. The two key pieces to protect the API structure are logging every request and monitoring for any signs of malicious activity.
9. Insecure Communication
If APIs communicate data in the clear, attackers can easily snoop on data in transit. It is safer to use secure protocols when passing data around, such as hypertext transport protocol secure (HTTPS).
10. Mass Assignment
This can be achieved through APIs binding data from user input to an object where attackers can change fields they ought not to access. To avoid this, you must ensure that only selected fields are editable for the users.
Because of these important threats, it becomes easier for developers to counter them and enhance their awareness of protecting API endpoints. Mitigating these risks will improve the security of API systems to protect valuable information.
IV. How to secure API: 7 best practices to consider
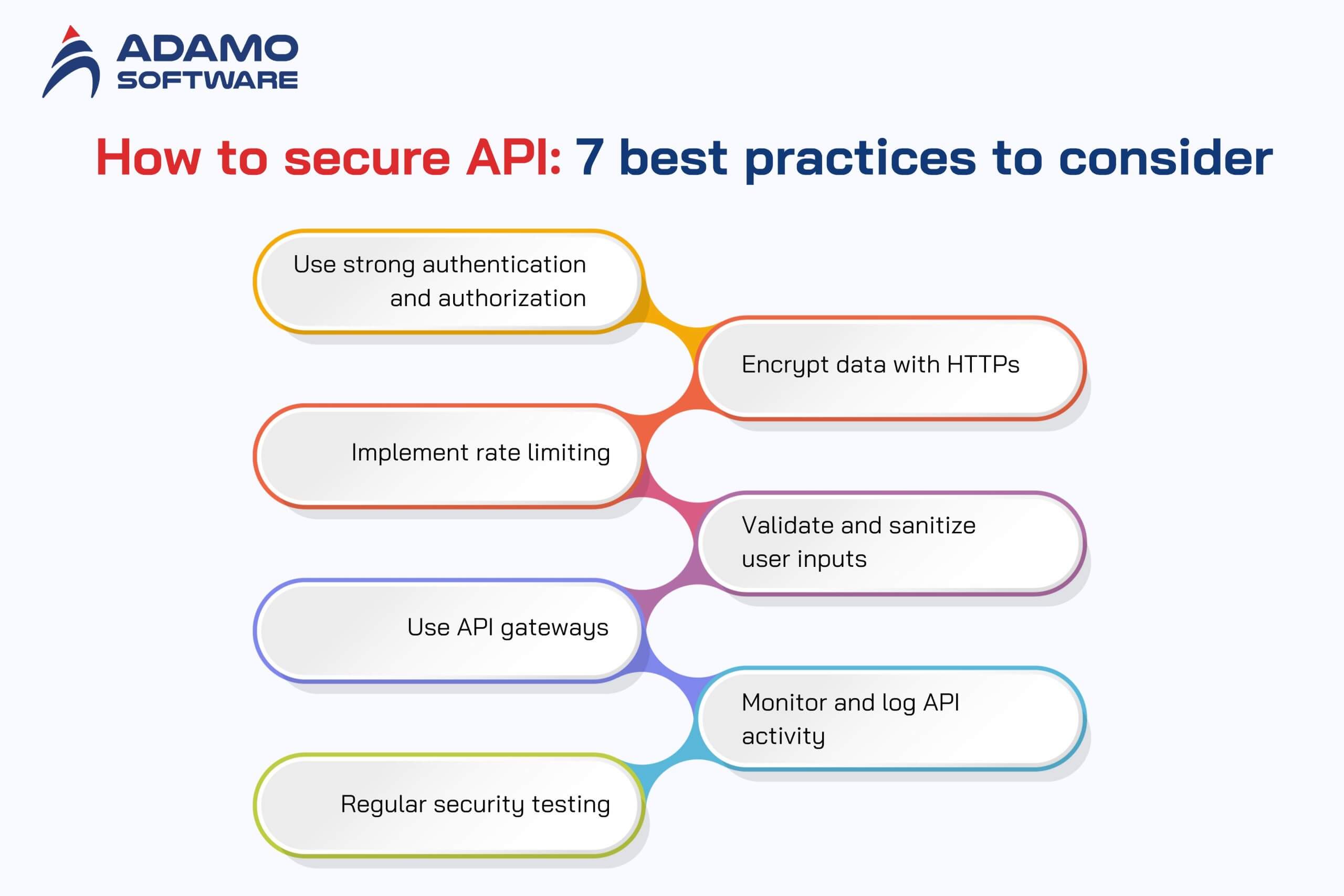
As noted in this article; to protect APIs, one needs to practice the best security measures available. APIs must have measures to protect from unauthorized access or data breaches. Thus, it is important to understand how to secure API systems. Below are seven essential best practices for securing your APIs:
1. Use Strong Authentication and Authorization
APIs must restrict access to entries by selecting a unique user security level that has logged into the system. Use advanced levels of security that include the following: OAuth, JWT (JSON Web Tokens), or consuming API keys. All in all, ensure controlled access to resources to ensure that every user has rights of access only to those fulminating resources that he or she needs. This is an important step in developing a good understanding of how to protect API endpoints from any unauthorized users.
2. Encrypt Data with HTTPs
It is recommended to always use HTTPS to secure the communication that happens between clients and APIs. Secure data transfer provides assurance that any information. For example, passwords or personal data cannot be intercepted during a transfer. To start with, enabling SSL/TLS encryption is considered the step toward securing API communication.
3. Implement Rate Limiting
Rate limiting is used to measure how many times a client may access an API within the stipulated period. This is useful when mitigating potential abuses. For example, in the form of Distributed Denial of Service (DDoS) attacks that flood your system. If you limit the number of API calls, then you are guarding your server and also learning how to secure API performance from high traffic.
4. Validate and Sanitize User Inputs
Applications that fail to validate or sanitize inputs can be susceptible to attacks such as SQL injection or cross-site scripting (XSS). Input validation enables the API to check if the data sent into it is correct, while sanitization is the process of eliminating any nasty code. For understanding how to protect oneself from various malicious inputs, this approach is necessary for how to secure API functions.
5. Use API Gateways
An API gateway is often referred to as an API front door, which is a single-entry point to all API’s. It assists to pull and manage security policies, routing, and monitoring traffic. Rate limiting, authentication, and logging are other features found in API gateways, making them a vital component of API architecture security, as explained in How to Secure API Architecture Effectively.
6. Monitor and Log API Activity
The actual users’ behavior tracking through the API brings opportunities to immediately notice irregularities and potential security breaches. Frequent monitoring and performance log checks enable one to identify and respond to a threat hastily. This is an important step to meet the knowledge of how to safeguard API systems by increasing visibility and response.
7. Regular Security Testing
Security employees should perform security tests on API, including penetration tests and vulnerability scans of different weak points. Security testing and auditing should be consecutively performed to enable you to counter other emergent threats. API protection is continuously important in keeping your API security on par because how to secure API will change over time.
The above best practices, when adopted, safeguard the users of API systems and content to help you learn how to secure API systems. Security should be given due importance to make your API secure and safe.
V. How Adamo Software can help

Adamo Software focuses on APIs as a Software as a Service provider and API security. As a strong team of developers, we provide enterprise-grade safe, speedy, and customizable API solutions for any industry. Consequently, Adamo ensures that the API we develop conforms to the best practices in preventing possible threats. Therefore, it assists organizations in learning how efficient API systems can be secured.
Adamo Software provides strong authentication and API encrypting and conducts everyday security reviews. The services provided by Adamo Software guarantee to secure your APIs from potential threats. We have API gateway technologies, traffic management, and security policies with optimization solutions. With Adamo Software, you can receive the tools to help you become an expert in protecting API infrastructure. Therefore, you will realize the activities you are preoccupied with.
If you are a business entity hoping to take your API security a notch higher, contact Adamo Software. We will help you understand how to secure APIs and provide an evaluation of your needs for securing your API environment.