What is Mobile Apps Security? Best Practices 2026

In the context of the constantly evolving digital mobility, mobile app security is one of the primary and at the same time multifaceted concepts referring to measures and tools needed to enhance the protection of mobile apps used on portable devices. Primarily, mobile application security is the careful integration of processes that aim at countering a range of threats, from advanced malware penetration to data leakage through insecure networks. This discipline requires mastery of app scanning techniques, and complex, highly developed automated systems designed to examine mobile application codes and configurations and pick out potential weaknesses that could threaten users’ privacy.
Thus, it becomes clear that the security of mobile applications requires the implementation of enhanced encryption techniques and strict authentication mechanisms with constant monitoring and preparation against any threats concerning the safety of users’ data as well as compliance with modern regulations.
I. What is Mobile Apps Security
Mobile apps security can be defined as the defense mechanism or strategy that has been put in place to ensure the protection of mobile applications from various security risks and threats. Living in a world where the use of mobile devices is almost essential in people’s everyday lives, the question of the need for secure mobile apps is beyond debate. This involves a holistic approach covering not only the software layer but also the hardware layer of the mobile devices and the information contained to prevent access of the information by unauthorized persons, leakage of information, and other cyber perils.
In its simplest understanding, mobile apps security is establishing strong security principles and processes to establish an effective security mobile app system. This incorporates the use of secure code, encryption both in transit and in storage, strong authentication, and authorization measures, and repeating security audits. It is to prevent possible security threats and guarantee that security threats are only a short amount of time and that they are eliminated.
Additionally, there are considerations of secure mobile apps against different kinds of threats like malware, phishing, and unauthorized access to data. This requires the constant assessment and modification of these measures to address new threats that may emerge and changes in the various cyber-attacks. Software solution providers are obliged to be wary and mindful of possible security risks and take desirable measures to make their solutions unassailable.
In conclusion, mobile application security is a complex area that refers to protecting the applications through careful preparation, monitoring, and implementing actions against threats. Major app security, therefore, can go a long way in helping app users feel safer and secure when using the applications in question, and this, in turn, will promote the overall trust level in such applications among their users.
II. Why Mobile Apps Security Important
It is therefore important to ensure that mobile apps are secured taking into consideration the use of mobile apps today in personal, business, and financial aspects.
Protection of Sensitive Information
Freemium apps usually process a significant amount of personal information that can be considered as personal identification data, money transactions, or secure messages. This data is exposed to insecure threats such as unauthorized access, data, and cyber-attacks resulting in financial loss and identity theft if the security of the mobile app is not well developed. The importance of having a detailed security plan for mobile applications reduces the risk of adverse effects and safeguards individuals who can suffer from it.
Defense Against Sophisticated Cyber Threats
It is, therefore, a common notion that cybercriminals always seek out new techniques to target the security weaknesses of mobile applications. Mobile apps security entails preventative measures that can be used to detect such incidences and prevent such vulnerabilities from being exploited in the app. This proactive approach is necessary to monitor and prevent new malicious attacks and to maintain the application’s security against new threats on the Internet.
Enhancement of User Trust and Confidence
Since the security and privacy aspects that customers are very sensitive to, they are more likely to use and appreciate applications that address this particular issue. Adhering to security mobile apps keeps the users engaged and possesses a good image, which is paramount to apps’ success and sustainability. The implication is that any security threats pose a major risk to an application’s reputation, users’ trust, and subsequent usage; besides the dangerous prospects of financial losses. As such, organizations must emphasize the security of mobile applications to sustain and increase users’ trust.
Regulatory Compliance and Legal Requirements
Some sectors like the financial sector or the healthcare sector have their policies and legal requirements regarding data protection demanding optimum security measures. Noncompliance with the above-regulated policies leads to severe ramifications and legal implications, making it crucial to have robust security features for mobile applications. It is important to keep security mobile apps in check for such requirements to enhance legal compliance and safe user data.
Safeguarding User Experience and Application Integrity
Ensuring mobile apps security is critical since this makes the layout protective and secure for users. This also contributes to the improved user experience of the application as well as protecting the application from vulnerabilities and future failures, thereby continuing its success and stability. A secure application means an application that does not pose any risk to the end user and their data and also helps maintain the reputation and functionality of the application.
III. How Does Security Mobile Apps Work
Mobile apps security is a process that involves the use of advanced technologies, vigorous processes, and implementable tactics that prevent mobile applications from being vulnerable to security issues. The primary aim is to keep the data safe, stop people who shouldn’t see it from getting access, and ensure the mobile app is private, always accessible, and works well with other systems. This involves a complex process of making a secure mobile app environment, and it includes several key parts.
Secure Coding Practices
Ensuring new code is written securely is the backbone of mobile application security. Programmers themselves need to follow certain guidelines and rules to ensure their code is immune to basic attacks like buffer overflows, SQL injection, or cross-site scripts, among others. Developing security into the software development lifecycle means that possible security vulnerabilities have to be spotted at an early stage thus preventing exploitation.
Mobile App Scanning Tools
Mobile app scanning tools play an important role in detecting such threats and mitigating related risks. These tools crawl through the code, configuration, and network usage of the application to identify possible security bugs. They give an overview of the specific weaknesses that were found which assists the developers fix such problems before the application is deployed. Regular practice of the mobile app scanning tools assures that fresh threats are detected and dealt with in real time.
Encryption and Data Protection
Among the most important things concerning mobile apps security is encryption. Such a way of coding helps to protect information not only while it is being sent but also while it is stored. Coding methods guarantee that all information sent through the app or saved in its storage is private and protected from exposure to unwanted eyes. This will help prevent unauthorized access and ensure more security for the data of the user, even if an attacker captures the device.
Authentication and Authorization Mechanisms
Security monitoring is another crucial requirement to help organizations track and respond to security issues in real time. This is done through the application of analytical and monitoring techniques which enable the detection of anomalous behavior and dangers. An incident response solution assists in fast and appropriate reactions to security incidents to reduce costs from compromised applications and their users.
Security Monitoring and Incident Response
Security audits and vulnerability scanning should be conducted in the mobile app ecosystem periodically. These practices involve conducting a mock attack on the application to determine the weaknesses present and the efficiency of the existing security solutions. This way the developers are always on the lookout for new threats that are likely to come up and keep on updating the application to make it secure all the time.
Regular Security Assessments and Penetration Testing
Regular security assessments, penetration testing included, are essential in keeping a mobile app environment secure. These are exercises whereby the application is attacked to reveal hidden vulnerabilities and test efficiency for security measures put in place. A periodic assessment will keep every developer ahead of increasing application threats.
To sum up, mobile apps security comprises of secure coding styles, mobile app scan tools, encryption, suitable authentication schemes, constant monitoring, and security audits. Through these measures, developers can design mobile applications that protect the information from threats, thus safeguarding users’ data and building confidence.
IV. What are the Most Common Threats in Mobile Apps
To be able to devise appropriate countermeasures that will provide security to the above mobile apps, it is important to know the most common threats in the mobile apps security domain.
Malware and Malicious Software
Malware is programs that take advantage of weaknesses in mobile applications and cause major security breaches, financial losses, and loss of public confidence. Therefore, measures that can be taken to manage these threats are critical to achieving strong security in mobile app environments. Malware continues to be among the most common threats that affect the security of mobile applications. Viruses and other malicious programs can sneak into a mobile device in a package with an innocent application, bought on an illegitimate market. Once installed, it can siphon off private data, monitor the user, and penetrate deeper by getting control of the device’s resources. This risk can be minimized by only downloading applications from reliable sources and constant and strict scrutiny of apps.
Phishing Attacks
Phishing is a scam where one tries to lure the other into surrendering his/her identification information and other sensitive details such as login details and financial information. These attacks are most often delivered through deceptive email, messaging, or pop-ups within the application. Raising the consciousness of users and integrating anti-phishing techniques into the mobile application minimizes the possibility of successful phishing attacks.
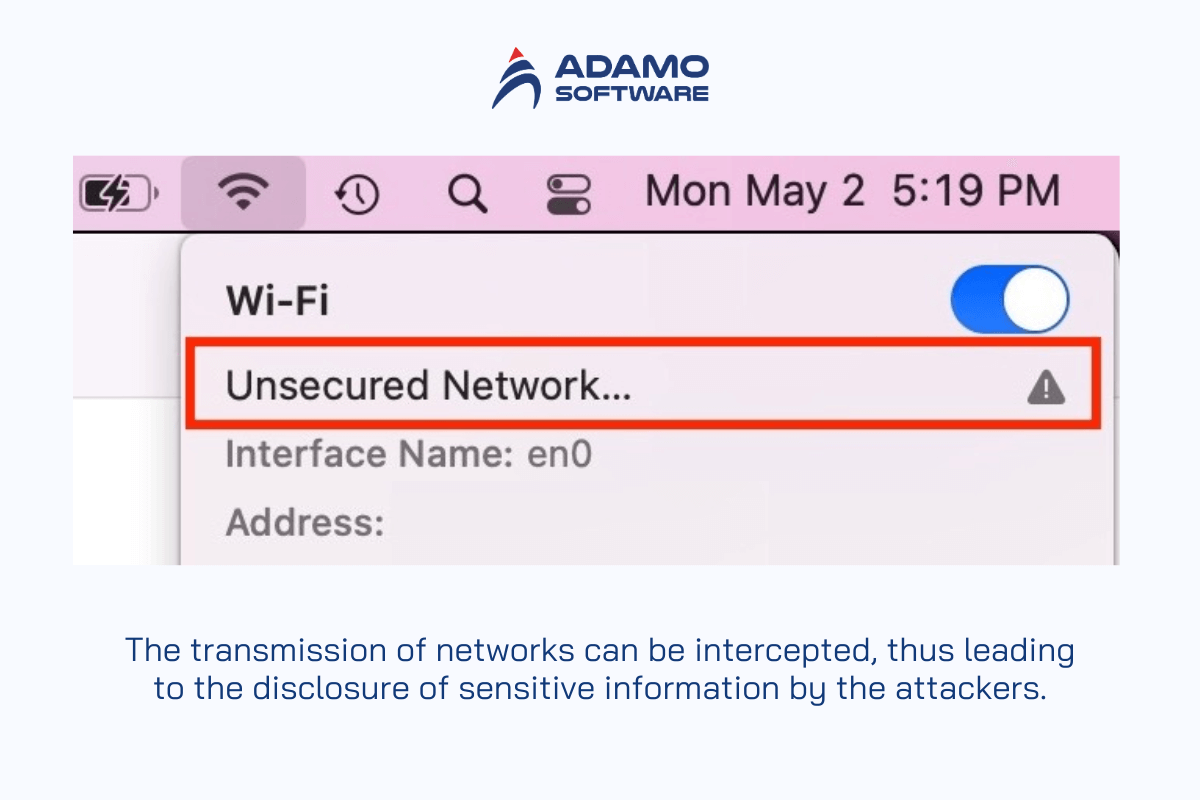
Unsecured Wi-Fi Networks
The use of unencrypted WLAN puts mobile devices at risk of various hostile actions. The transmission of these networks can be intercepted, thus leading to the disclosure of sensitive information by the attackers. Mobile apps security could be improved only by adopting strong encryption strategies on the application’s side and informing the users about the risks of performing financial transactions on the Wi-Fi networks that are available for public use.
Inadequate Authentication and Authorization
The lack of adequate authentication and authorization processes is one of the greatest risks that can be identified in mobile applications. Inadequate login methods and weak access control measures create weaknesses by which intruders can easily access sensitive data. It is critical to improve security within security service mobile app environments by expanding the measures used in authentication, like the adoption of multi-factor authentication and proper session management.
Data Leakage and Insecure Data Storage
Data leakage refers to a situation whereby data considered confidential in one way, or another gets passed on or transmitted to entities that are not supposed to receive it. For example, they are storing your password in plain text on the device or in cloud storage.
Insufficient Code Obfuscation
The absence of code obfuscation means that the attackers can comfortably reverse engineer the mobile applications and thus get to understand many of the secrets of the application and its logic, along with many of its weak points. By applying code obscure approaches, the likelihood of attackers understanding the application’s code to exploit it becomes much tougher.
Man-in-the-Middle (MitM) Attacks
Intercepting is another type of attack that may occur when an attacker tries to forge communication between a mobile application and a server and intercept the data transferred between them. Developing robust encryption techniques, secure socket layer (SSL), and transport layer security (TLS) can also protect the transmission of information and prevent an attacker from performing a MitM attack.
Inadequate Security Testing
Not conducting security testing at all phases of the software development life cycle exposes this mobile application to several risks. Security assessments should be undertaken regularly in the form of penetration tests and vulnerability assessments to devise security issues that can be exploited.
In conclusion, the threats facing mobile apps security are Malware, Phishing, unsecured Wi-Fi, inadequate Authentication, Data leakage, Insufficient Code obfuscation, MitM, and Inadequate Security testing. It is only by identifying these threats and reversing them that a better security service mobile app environment can be achieved, with users’ data being secure.
V. Best Practices Boost Mobile Apps Security
To improve the security of mobile apps, it is crucial to adopt a complex approach based on the use of technologies, strict adherence to industry standards, and the use of preventive measures. Through the practice of IT best practices, developers can protect their applications against different risks and make them safe for users.
1. Implement Secure Coding Practices
There is a need for developers to follow secure coding best practices to avoid things like buffer overflow, SQL injections, and cross-site scripting. Adhering to the best practices and standards promotes the stability of the application to withstand any existing security vulnerabilities. It is recommended to use a ‘code review’ best practice as well as automated static code analysis tools to detect and eliminate potentially dangerous gaps in the early stages of the development cycle.
2. Use Strong Encryption Methods
It is significant to maintain the confidentiality of the information both during transmission and while it is stored on the device. Encryption and decryption techniques deployed mean that even assuming the data is intercepted, it is still incomprehensible to the intruder. Proper deployment of SSL/TLS for data transfer and encryption of local storage can significantly improve the security of mobile apps.
3. Employ Robust Authentication Mechanisms
Other measures include MFA and BIO, which are more stringent compared to simple passwords. They are effective ways of guaranteeing that only legitimate users access the application and the data. Additional strength to the authentication processes is offered by secure session management practices.
4. Conduct Regular Security Assessments and Penetration Testing
Security audits should be conducted regularly, including vulnerability assessments and penetration testing to evaluate potential risks.
These simulations include assessments to test attacks that portray real-world scenarios to validate the efficacy of existing security controls, thereby providing feedback on potential areas for improvement.
5. Utilize Mobile App Scanning Tools
Automated mobile app scanning tools play a vital role in detecting security vulnerabilities and their remediation. They will do an exhaustive lookup inside the application code, configuration, and network interactions. In-depth reports are provided for the identified issues. In this way, regular scanning would ensure constant monitoring and prompt remediation of vulnerabilities.
6. Secure Data Storage
Implement safe data storage to avoid the chances of data leakage. Sensitive information is stored in an encrypted form. Furthermore, access controls create an entryway only accessible to authorized people. As much as possible, avoid storing sensitive data in local storage and follow safe container practices for such data.
7. Obfuscate Code
Obfuscation of the code makes it very hard to reverse-engineer a mobile app. In turn, this protects the logic and sensitive information of the application. Developers can use code obfuscation techniques, which obscure or even conceal the code from potential misuse by such ill-minded users.
8. Educate Users on Security Best Practices
User education is a vital component of mobile apps security. Informing users about the importance of downloading applications from trusted sources, avoiding unsecured Wi-Fi networks, and recognizing phishing attempts can significantly reduce the risk of security breaches. Providing clear and concise security guidelines within the application can empower users to adopt safer practices.
9. Implement Strong Access Controls
A mobile app has stringent access control measures in place for the sensitive parts, allowing only authorized personnel to access them. RBAC/Least Privilege: It should apply role-based access control and follow the principle of least privilege; this will ensure the risks due to people accessing resources without appropriate business needs are reduced. Regular audits of access controls would be instrumental in keeping them effective.
10. Keep Software and Libraries Updated
Keeping the app, its required software and other tools, up to date is important for keeping a mobile app safe. These updates fix known problems, helping the app stay safe from new dangers.
VI. How Adamo Ensures Mobile Apps Security in Our Software Solution
At Adamo mobile apps security, we consider integration as a primary requirement in our software development process. To mitigate several types of security threats our organization uses a holistic approach that includes both technology-based safeguards along with strict procedures and anticipatory methods. Mobile apps security has not been treated as an afterthought at Safe Zone, rather, it forms a strong foundation of all our software solutions that we offer to clients, from conceptualization to implementation and support.

Secure Development Lifecycle
Adamo abides by a secure SDLC while incorporating security into each phase of our software development process. This essentially means we integrate safe coding practices, frequent peer code reviews, and automatic static code analysis tools to spot and fix any possible vulnerabilities at the earliest opportunity. Following industry standards and guidelines will harden applications against common security threats.
Advanced Encryption Techniques
Adamo adheres to a secure Software Development Life Cycle to build in security in every phase of software development. This would pertain to secure coding practices, periodic reviews of code, and the implementation of state-of-the-art automated static code analysis tools, all aiming at the early detection and fixing of plausible vulnerabilities. Following industry standards and best practices will make our applications resilient to common attacks.
Comprehensive Authentication Mechanisms
We return priority to the protection of sensitive data by advanced encryption techniques; all data is encrypted, both in transit and at rest. To this end, it remains inaccessible to any entity not authorized. That means our security strategy for mobile apps incorporates SSL/TLS protocols for data transmission and secure data storage practices.
Regular Security Assessments and Penetration Testing
Adamo deploys thorough authentication mechanisms to prevent unauthorized access to our applications. In this respect, we use multi-factor and biometric authentication and secure session management to ensure that only properly authorized users can access our applications and their data. These robust authentication methods are designed to provide an additional layer of security and enhance user trust.
Utilization of Mobile App Scanning Tools
Using sophisticated mobile application scanning technologies, we effectively mitigate risks associated with apps. These tools offer a full analysis of our application’s code, settings, and network traffic while reporting findings about discovered deviations. The latter could mean that constant scanning provides for consistent check and repair of the weakness.
Code Obfuscation and Secure Data Storage
This is done to prevent reverse engineering of the applications and data leakage and in turn, Adamo uses code obfuscation and secure storage of data. By wrapping our code, we essentially make it harder for the attackers to penetrate through our applications. Furthermore, we guarantee that any data is securely stored and encrypted, thus minimizing the chances of its confiscation by different individuals.
User Education and Awareness
Adamo believes that user education is critically important in ensuring the security of mobile apps. Our security measures include the use of comprehensive and easily understandable messages to invitee users and the public on how to protect their applications, including creating awareness of the need to download applications from trusted sources and avoiding unsecured W-Fi networks. In other words, the protection of our applications is improved by giving users strength in the form of knowledge.
Continuous Updates and Patching
We understand that it is compulsory to update the software and libraries we have been using frequently. Adamo updates and patches the applications often to fix any uncovered vulnerabilities and to strengthen the security. It also aims to make our software constantly secure from any such threat that might arise in the future.
VII. F.A.Qs about Mobile Apps Security
1. What is mobile apps security?
Mobile app security is a broad term that encompasses all the measures and practices used in the security of mobile applications against security threats and risks. This includes measures like encryption, authentication, secure data management, and constant vigilance to protect the app and the data it contains or processes. Mobile app security is essential to prevent malicious third parties from gaining access to users’ details and eroding customers’ confidence.
2. Why is mobile apps security important?
Mobile apps security is essential since it enhances the security of user data in cases of unauthorized access, cyber-attacks, and data breaches. Focusing on security mobile apps allows companies to follow the regulations and avoid significant financial losses, reputational damage, and user trust loss. As proven in this paper, the integration of mobile application security solutions is crucial in enhancing the well-being and stability of an application and in establishing a safe and reliable platform for users.
3. How do mobile app scanning tools work?
Mobile app scanning tools are comprehensive automatic solutions that check the source code of the application, its settings, and network traffic for potential threats. These tools can do full scans which give out reports of areas that require attention to be given. Routine scanning using mobile app scanning tools ensures that there is a constant check on mobile app security and quick fixes for the security threats that may be discovered.
4. What are some common threats to mobile apps security?
Some of the risks affecting mobile apps security are malware, phishing, insecure connections, limited authentication, leakage of data, weak code obscuration, and MitM. It is important to be familiar with these threats to be able to apply adequate measures for mobile application security. If these vulnerabilities are fixed, developers can design better security mobile applications that protect user information and enhance user security.
5. How can developers enhance mobile app security?
Mobile apps security can be improved by developers practicing secure code writing, using strong encryptions, and implementing strict authentication such as multifactor authentication. It is imperative to perform monthly security audits and assessments such as penetration testing and vulnerability scan. Using the mobile app scanner to periodically scan for threats, proper accreditation of data storage, and giving out security tips are also important strategies. These combined efforts ensure that security mobile apps are well protected against new threats and risks as the future holds.





