Crypto Wallet Development: Types, core features and build process

Explore Crypto Wallet Development with clear guides on features, roadmap, and wallet types to help businesses launch secure and scalable blockchain products.
The development of a Crypto Wallet is proving to be one of the most significant steps any business should take when entering the digital asset space. Businesses desire a secure tool, and consumers desire the ability to store, send, and receive cryptocurrencies easily. Due to this reason, numerous teams are seeking ways to make wallets that are safe, fast, and easy to use. The sphere evolves rapidly, and it is better to know the fundamentals of how to make reasonable decisions and prevent typical pitfalls.
Cryptocurrency Wallet Production is becoming increasingly available as technology is being expanded. Programmers now possess more appropriate frameworks, guidelines, and methods that have been tested. A business has numerous options for the type of wallet and its features. They may also make a decision on whether to develop a tailor-made solution or depend on an off-the-shelf product. Having the right roadmap, the process will be smoother and more predictable.
I. What is a cryptocurrency wallet?
A crypto wallet is a web-based application that can assist users in storing, transferring, and acquiring crypto assets with security and freedom. It is not full of real coins as a real wallet is. Rather, it secures the personal secrets that allow users access to their blockchain money. The wallet signs the transaction and verifies the ownership as a person makes a transaction. This maintenance makes the assets safe and it enables users to transfer money anytime.
Crypto wallets also display your balances and activity records. It can communicate with various blockchains to allow every update to pass through them. It operates by using two key factors. The first factor is a public key which serves the purpose of being an address. Here you can receive funds. The second factor is a private key which should remain confidential. It provides you with complete access to your assets.
When the two keys are combined, the users can control their money without the involvement of banks or even intermediaries. This is the reason why wallets are significant to Crypto Wallet Development. Accessibility and safety should always be considered hand-in-hand.
The current cryptocurrency wallets are not mere storage systems. Supports such features as multi-currency management, smart contract interaction, and in-built identity checks are now supported. Most of them also have backup and recovery systems to ensure that the users do not lose their assets. Since the crypto market is expanding rapidly. Crypto Wallet Development pays attention to the creation of a wallet that would be secure, adaptable, and user-friendly to less skilled and more experienced users. A good wallet will give the basis of any blockchain product. It assists businesses in inspiring confidence among their users.
II. What are the main types of crypto wallets?
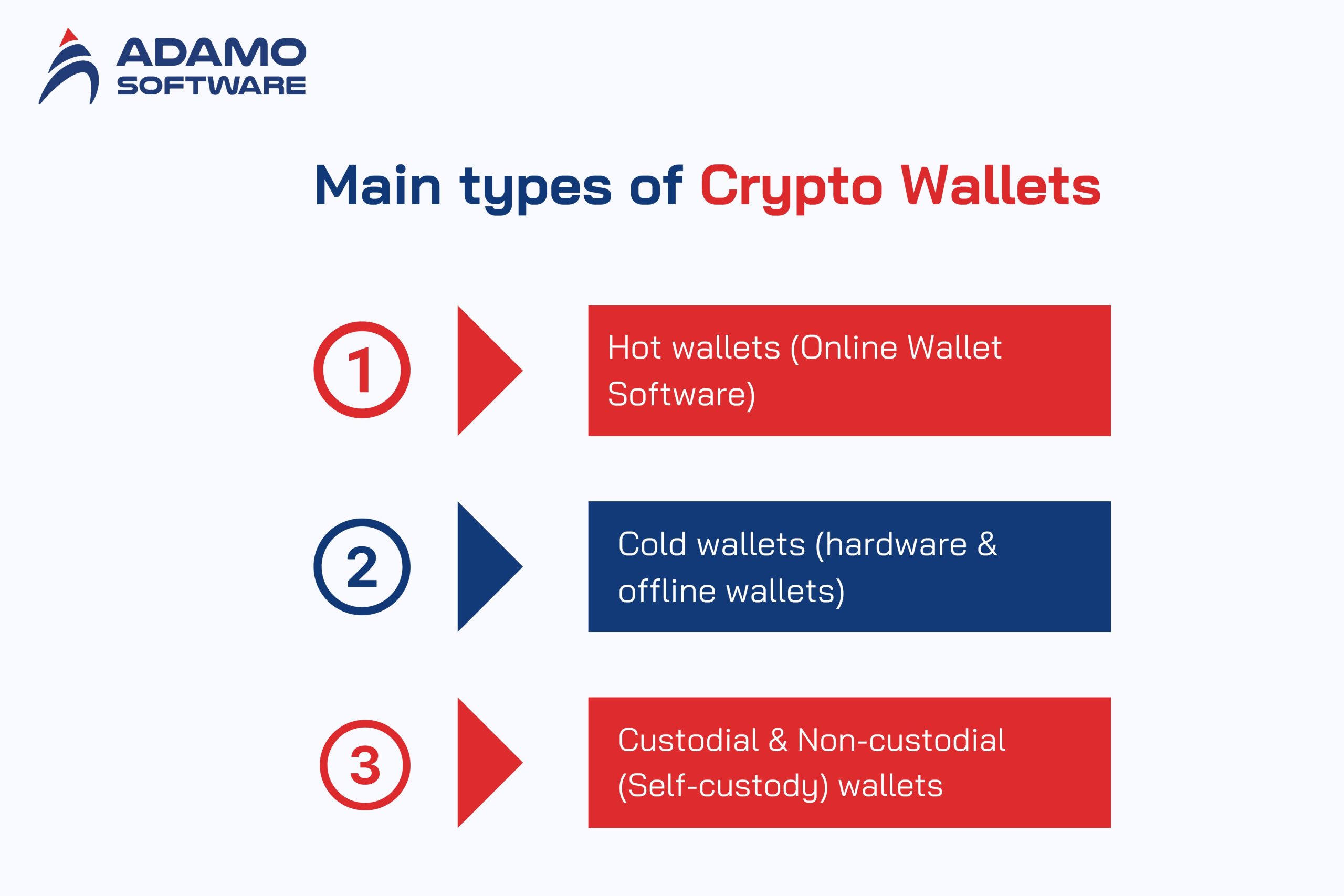
Cryptocurrency wallet development is a field where one should be familiar with the primary wallet types. The wallets differ in the way they store private keys. They are linked to the network, and the parties in control of the wallets. All types are appropriate to users and purposes.
1. Hot Wallets (Online wallets software)
Hot wallets are operated on devices that are linked to the internet. These are desktop software or mobile apps, or web-based browser wallets.
Pros:
- Very easy to set up and use.
- Quickly sending or receiving crypto.
- Daily practice is friendly.
Cons:
- Being more affected by hacking, phishing, or device vulnerabilities.
- Not as safe to store a large sum of crypto long-term.
- User practices (level of password strength, safety of devices, and so on) are critical to security.
2. Cold Wallets (Hardware & Offline Wallets)
Cold wallets also contain dedicated hardware, or even more basic offline storage techniques (although hardware is much more widespread and secure).
Pros:
- The online keys imply significantly reduced vulnerability to attacks.
- Ideal for long-term storage or for looking after large quantities.
- Complete peace of mind is ensured if the user keeps and stores the device safely.
Cons:
- It requires a device to be used, and downloading the amounts is slower than hot wallets.
- The possibility of loss, damage, or forgetting the place where you stored the device.
- It’s not suitable when a user must access it regularly or for fast trades.
3. Custodial and Non-Custodial (Self-Custody) wallets.
This axis explains the control of the privies. Your wallet may be hot or cold, but custodial or not is irrelevant to the ownership and responsibility of the user.
Custodial Wallets
Custodial Wallets are private keys that are stored by a third-party provider (such as an exchange or service). Funds are accessed using the credentials of the account.
Pros: It is easy to use without the necessity of key management; Recovery can be easily done.
Cons: The User must rely on the provider; Their money can be stolen or squandered in the wrong hands, or the provider handles keys improperly; The user has less control.
Non-custodial (Self-Custody) Wallets
These wallets are those whereby the user retains his or her own private keys (locally or on his or her hardware). No third party has access.
Pros: Complete control and ownership; Additional privacy; Consistent with the philosophy of decentralization.
Cons: User has complete responsibility – the loss of keys or seed phrases may result in the loss of money, without any third-party backup.
III. Must-have features for Crypto Wallet Development
Any powerful crypto wallet must have a consistent series of features, which include safety, onboarding, and easy handling of assets. You must create features that keep your users safe. However, you should make the processes that people must follow in their daily routines quick. The users have come to demand easy sign-in, secure storage, swift alternating, and precise control of their keys.
The right characteristics minimize the errors of the users, decrease operational risk, and enhance trust. You can also have your product scaled to thousands of active users using them.
And a study of the MIT Digital Currency Initiative observes that basic UX flows lower the cases of key-loss by the user by a factor of four or five.
These results explain the importance of must-have features in Crypto Wallet Development.

1. User Protection and Secure Key Management.
Every wallet is pegged on security. A wallet might be beautiful though without the power of protection in terms of key power; it cannot work.
Key elements:
- Client-side key generation: The wallet generates keys on the device and thus no one can ever see the key.
- Biometric/PIN authentication: Face ID, fingerprint, or secure PIN to approve actions.
- Key storage: There is encrypted storage of keys in an enclave or an encrypted key vault.
- Option 1 MPC or seedless: Weakness any apprehension of losing a 1224-word seed phrase.
- Auto-log out, and session registration: This eliminates the possibility of third parties accessing your computer.
Why it matters:
The layer avoids hacks, phishing, and unauthorized transactions. It also minimizes the chances of users losing their assets because they do not store them well.
2. Painless Onboarding and Obligatory Recovery.
Users drop out because they are onboarded when it is too complicated. Crypto Wallet Development should be concerned with easy steps.
Key elements:
- Quick registration: Email, telephone, or passkey (non-custodial and MPC compatible).
- Step-by-step configuration: Sets of clear steps showing how it is done.
- Flexible recovery solutions: Seed phrase backup, MPC, social recovery, or encrypted backups on the cloud.
- Bookmark sharing: The user system can travel across machines maintaining a secure system.
Why it matters:
This minimizes drop-offs and has made the wallet beginner friendly. It also reduces the number of support requests that are made by users who lose access.
3. Basic Transaction / Asset Management Instruments.
After installing the wallet, users require straightforward tools to transfer, accept, and administer assets.
Key elements:
- Multi-chain support: Ethereum, Bitcoin, BNB Chain, and Solana, etc.
- Address book: Stores often use addresses and label them.
- QR code scanning: Speeds up sending and receiving as well as eradicates typing mistakes.
- Balances in real-time: Customers can view the right value of their holdings in real-time.
Why it matters:
Individuals require clarity in their money transactions. These applications eliminate mistakes and make people trust their wallet
These characteristics enhance interaction and prolonged memorization:
- Swapping in-app (constitutes DEX integration).
- Push (price changes, transaction alerts) notifications.
- Portfolio analytics (history, profits/losses, intra-day, southern ore, etc)
- Web 3 dApps In-app Browsers (finance) that are used to use or navigate DeFi (Web3) in non-fungible assets NFTs non-fungible trading (Web3) in non-fungible games NFTs
- Gallery support that is safe with metadata.
- Optimization of fees and automation of settings.
- Online chat (customer service) or ticket system.
These supplements make your product complete and current.
IV. A complete development roadmap to develop a crypto wallet
The process of making a crypto wallet is a progressive one. The stages generate trust, security, and a good user experience. The roadmap will ensure teams do not make any errors and produce a powerful product. In the case of Crypto Wallet Development, one should take small steps at a time and perform testing frequently and select only the tools that will help you consider your actual business expectations.
According to research by Stanford University, Cybersecurity Center, more than half of security failures of blockchain applications are due to poor planning of development and a lack of testing stage.
In a separate report released by the European Union Agency on Cybersecurity (ENISA), it was demonstrated that systematic developmental cycles minimize security cases by as much as 4%.
These figures demonstrate the need to have a proper development roadmap.
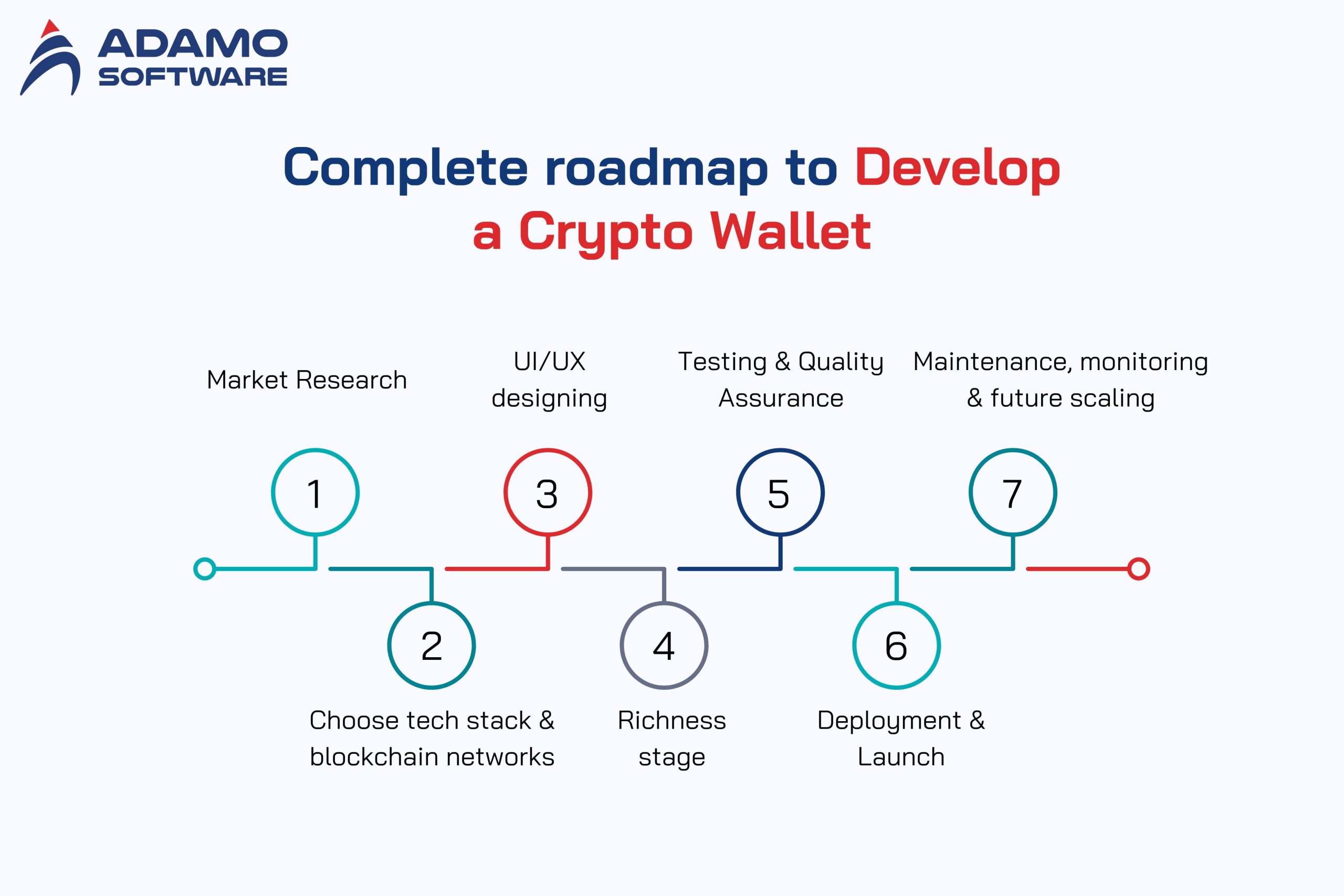
1. Market Research/Requirements Definition.
This is what your project must be based on. You need to research your users and your business requirements before writing any code.
Key steps:
- Target your audience: Trader, NFT customer, beginner, enterprise customer, or DeFi customer.
- Select wallet type: Custodial (wallet), non-custodial (wallet), MPC (wallet) or MultiSig (wallet), or smart contract wallet.
- Channels of selection: Mobile, desktop, browser extension, or cross-platform.
- Competitors of the study: Check what users expect by studying competitors: MetaMask, Coinbase Wallet, and Trust Wallet.
- Regulatory requirements: KYC, AML, regional, API.
Goal of this phase:
Develop a well-defined product scope to make sure the developers and designers are fully aware of what they are developing.
2. Choose Architecture, Technology Stack & Blockchain Networks
In the case of Crypto Wallet Development, performance, cost, and security are determined at the stage of architecture.
Key steps:
Pick blockchain networks: Ethereum, Bitcoin, BNB Chain, Solana, Polygon, Tron, or multi-chain.
Decide wallet architecture:
- MPC for seedless onboarding
- Local key storage non-custodial
- Server-side protection with custodial.
- Automation in Smart Contract Wallets.
Backend technology: Node.js, Go, Rust, or Java.
Frontend frameworks: React, Vue, Flutter, or React Native.
Add necessary APIs:
- Web3 libraries
- RPC providers
- Price feed APIs
- Analytics tools
- Goal of this phase
Establishing a firm technical foundation can grow in the long term.
3. UI/UX Designing and User Flow Charting.
Cryptocurrency users tend to abandon apps that are perceived to be complicated. A clear design is essential.
Key steps:
- Establish user processes: Sign-up, signing transactions, swaps, and recovery procedures.
- Make easy screens: Have simple buttons, readable typeface, and minimized behavior.
- Via add-on boarding screens: Tutor the users to protect keys and avoid fraud.
- Design visual identity: Icons, Color schemes, animation, and brand design.
- Prototype and test: Determine whether the users can comprehend every step without difficulty.
This phase ensures that the wallet feels comfortable, approachable, and easy to use even for novices.
4. Richness (Frontend, Backend, Blockchain Integration) Stage.
And here is where the wallet comes into existence.
Key steps:
Frontend development:
- Construct dashboards, portfolios, transaction history, and settings.
- Inclusive QR scanner features, address book, and multi-account.
Backend development:
- Develop customized server logic or non-custodial secure communication server logic.
- Vert push notifications, analytics, and logging tools.
Blockchain integration:
- Implementing Web3 libraries.
- Connect RPC endpoints.
- Add multi-chain support.
- Build transaction signage.
Security integration:
- Biometric login
- Encrypted key storage
- Anti-phishing protections
- Fraud alerts
This phase Designs a working, safe, and reliable app to meet the expectations of the user.
5. Testing & Quality Assurance
Testing is not optional. Safe Crypto Wallet Development is centered upon it.
Types of tests:
- Functional testing: Receive, send, and exchange work.
- Security testing: Key protection tests, legal vulnerability scan, penetration tests.
- Performance testing: Network handling, loading time, and speed.
- Multi-me devices: iOS, Android, assorted browsers, and outdated phones.
- Blockchain simulation tests: Fees, congestion, seam cases.
Goal of this phase:
To identify issues at an early stage and defend the users until release.
6. Deployment & Launch
The wallet is now ready to be tested.
Key steps:
- Install RPC connections and server machines.
- Post App Store and Google Play mobile apps.
- Publish a browser extension to Chrome, Firefox, or EDG.
- Empower analytics and monitoring dashboards.
- Procure customer scripts and frequently asked questions.
This phase helps Crash-free automatic rolling start and no confusion for the user.
7. Maintenance, Monitoring, and Future Scaling.
Crypto wallets do not have anything whatsoever that is final. They need constant updates.
Key steps:
- Add new networks and tokens.
- Improve security patches.
- Fix performance problems and bugs.
- Launch new products such as staking or an NFT module.
- Observe user behavior using analytics to identify UX issues.
This phase helps to maintain the wallet as being safe, innovative, and competitive.
V. Custom vs Off-the-shelf crypto wallets: Which one suits your business
The decision to go with the custom wallet or an off-the-shelf solution is one of the most significant ones in Crypto Wallet Development. All the variants have varying extents of control, pace, cost, and flexibility in the long term. It will be up to you and your objectives with the project goals, your security requirements, and the speed with which you desire to enter the market.
| Criteria | Custom Crypto Wallet | Off-the-shelf Crypto Wallet |
| Time to Market | It takes a longer time to develop since all the features, design, and security levels are developed out of the box. Best suited when the team desires a long-term product. | Prepared much quicker as the main system is already in place. Suited to rapid release and testing the new product in the marketplace. |
| Upfront Cost | The budget requirement is larger: the team constructs the complete system and architecture. The long-term costs are controllable. | Reduced start-up cost as the majority of functions are off-the-shelf. But frequent fees or updates might be incurred in future. |
| Ownership & Intellectual Property | Title to the codebase and product logic. It is entirely up to you as to what happens with the wallet. | No ownership over the internal code, this is considered to be usually no. You license the technology to use the technology, but you cannot have control over the base design. |
| Customization Level | Very high freedom. You may re-design the interface, add chains, custom smart contract integration, or come up with other things. | Limited freedom. There can only be superficial modification, and fundamental mechanics cannot be modified entirely. |
| Security Structure | Security may be built precisely as required for personal encryption, multi-tiered security, and special recovery. | Security comes after the vendor’s design. The architecture may not be available to you, and this decreases transparency. |
| Ability to Scale | Simple to scale with the increase in your user base. You command the backend. Therefore, you may improve performance and incorporate more blockchain networks. | Scaling is based on the limits of the system of the provider. And in case the vendor is incapable of scaling, your application will also slow down. |
| Revenue & Monetization Options | You have the option of building your own revenue models – fees, premium tools, staking, swaps and custom financial services. | Options to monetize are limited. One can only add what the provider supports or tolerates. |
| Maintenance & Updates | View updates, blockchain integrations and bug patches are dealt with by your team (or partner). You determine the time and manner of improvements. | The provider takes care of updates. You have to stick to their timetable and take their restrictions. |
| Integration With Web3 Ecosystems | Easy to interoperate with all types of DeFi platforms, DApps, exchanges, or any service to the chain since the protocol is one hundred percent open to customization. | The decisions of integration are based on what is already supported by the provider. New connections might not be an option. |
| Brand Strength & User Trust | Drives up brand loyalty since the wallet is unique and is capable of working to your expectations. Users see it as premium. | More difficult to shine since there are numerous apps with identical templates. The product is not so unique. |
| Long-term Strategic Control | You manage all the components of the roadmap. There are no external limitations when you can grow, pivot, or expand at any point. | Plans will be based on the choices of vendors in the long term. Any pricing or policy adjustment can have a direct impact upon your business. |
| Regulation & Compliance | To some extent, compliance features can be integrated. The regional laws, audits, and KYC/AML rules are easy to meet. | There are few compliance instruments. Your policy updates are based on the updates provided by the vendor to remain in touch with regulatory requirements. |
| Support for New Blockchains | The addition of new chains can be done at any time the business requires them. Flexibility is unlimited. | Will have to wait till the vendor can support new networks. This decelerates innovation and suppresses the product’s growth. |
How to Choose the Right Option for Your Business
In the crypto wallet development work, just answering three straightforward questions would suffice:
- Do you need unique features? The option to select custom is offered in case of sophisticated security, special user flows and logic as in a chain which may be required.
- How fast do you need to launch? When the speed is given, go off the shelf.
- What is your long-term vision? When you are planning to scale, combine with new protocols, or develop a complete ecosystem, then custom development is more sustainable.
VI. Final thoughts

The initial steps to a successful wallet project are a proper plan and appropriate architecture. Your decision be it custom or off-the-shelf must be based on your users’ needs, your security requirements, and your vision of your business in the long run. A custom solution developed thoughtfully is usually the right way to go in case you may need to scale, support multiple chains, or to include custom features.
Security must remain in the limelight. Security key handling, solid authentication, rigorous testing, and maintaining it should not be an option. Adamo Software, as a development partner, consists of experienced deep blockchain and fintech with professional engineering and QA processes.
Finally, usability matters. The wallet should be simple to use for beginners but strong for advanced users. Product Good UX, well-defined recovery flows, convenient multi-chain support — assist in adoption and user trust. With the increase of blockchain applications in the global business environment, a developed wallet can turn into a fundamental resource for any company.
FAQs
1. How long does Crypto Wallet Development usually take?
A normal project lasts between 3-6 months. An MVP with a simple send and receive interface will be finished much sooner, whereas a multi-chain wallet comprising staking, swaps and more intricate security is a longer-run project. The timeline is based on design, integration, security testing, and the support of blockchains. Planning reduces the project time schedule, and scope gives no room for delays.
2. How much does it cost to build a crypto wallet app?
The development of a Crypto Wallet typically costs between 40,000 and 200,000/+. The last budget is based on what you want, how many chains, what are its UX features and what is its level of security. A non-custodial wallet will be cheaper, whereas a completely non-off-the-shelf solution that is also provided with the features of the smart contract and the advanced analytic solution is more expensive. The long-term cost is also contributed by maintenance and updates.
3. What features are essential for a modern crypto wallet?
The features that require the must-have are:
- Onboarding and backup security.
- Send, receive, and swap capabilities.
- Multi-chain support
- Live balance and history of transactions.
- Push notifications
- Biometrics or PIN
- Recovery flow
When developing a crypto wallet, feature additions such as staking, Non-Fungible Tokens, portfolio management, and fiat on ramps may be used to make your product notable.
4. Which blockchain networks should I support first?
The chains that your users require the most are to be started first. Bitcoin, Ethereum, BNB Chain and Tron are among the many wallets that started off with huge communities. Include chains such as Polygon, Arbitrum, or Solana, in case your project is aimed at DeFi users. Multi-chain support is simpler when modular architecture is used in Crypto Wallet Development in the first instance.
5. What is the difference between custodial and non-custodial wallets?
Custodial wallets keep user keys in a server hence the users do not have control over the keys. They are convenient yet they require a powerful infrastructure.
People can have full control of the keys in non-custodial wallets. They are more privacy-and security-assured, though the user must safeguard his seed phrases.
The decision made by you influences the entire Crypto Wallet Development process since the database, security model, and compliance rules are divergent.